1. Create your local user(s): User > Local > Create New
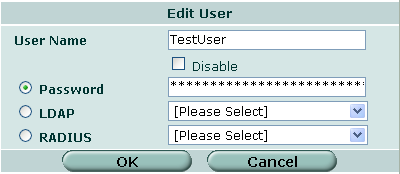
2. Add the user to a new group: User > User Group > Create New
Make sure the type is set to "Firewall" and add the user to the members section.
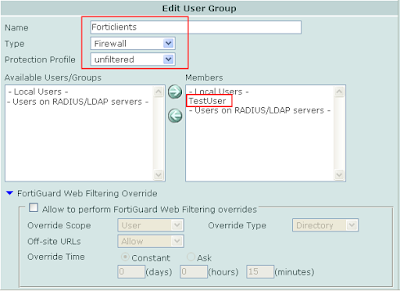
3. Phase 1 VPN: VPN > IPSec > Create Phase 1
Create a new phase 1 with the options selected below. Fortinet recommends Aggressive mode but I have found that it also works well with Main Mode. Fortinet also recommends using Peer IDs but once again, this way works as well.
Notice that this is going to be a dialup tunnel so, therefore, Interface mode is not enabled. Dont forget to select Xauth with the apporiate group.
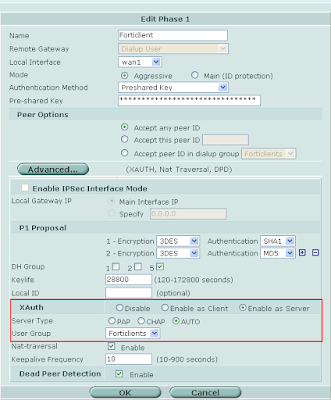 4. Phase 2 Tunnel: VPN > IPSec > Create Phase 2
4. Phase 2 Tunnel: VPN > IPSec > Create Phase 2Enable "DHCP over IPSec" and add the source and destination addresses.
5. Now Create a new DHCP Server: System > DHCP > Internal > Add DHCP Server
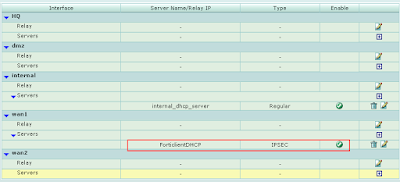 6. Configure DHCP Server:
6. Configure DHCP Server:Make sure the type is set to "IPSEC" and the range that you want your Forticlients to pull is not already being used on your network. The Default Gatway will be the IP of your Fortigate Device.
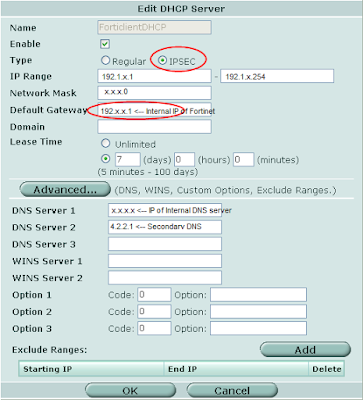 7. Create Address of Forticlients Range: Firewall > Address > Create New
7. Create Address of Forticlients Range: Firewall > Address > Create NewFor demonstration purposes our range will be 192. 1.x.[1 - 254]. Notice the format required for defining ranges in Firewall Addresses.
 8. Create 2 Policies: Firewall > Policy > New
8. Create 2 Policies: Firewall > Policy > New2 Policies are required in order to make this work. One will be used for the DHCP service and the other for client traffic.
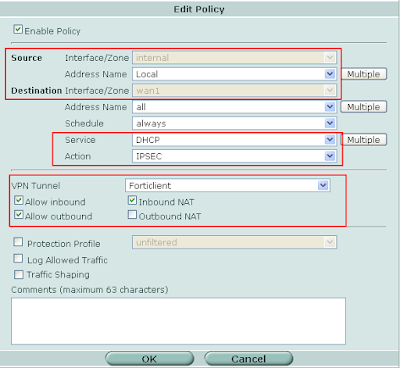
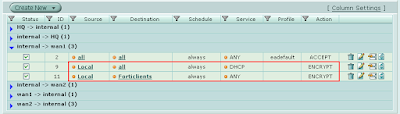 9. DHCP Policy:
9. DHCP Policy:Make sure the service selected is "DHCP" with the action of "IPSEC". Select the correct tunnel and select "Allow Inbound", "Allow Outbound", and "Inbound NAT" as it is displayed below.
Notice that the address name is set to "ALL" in this policy.
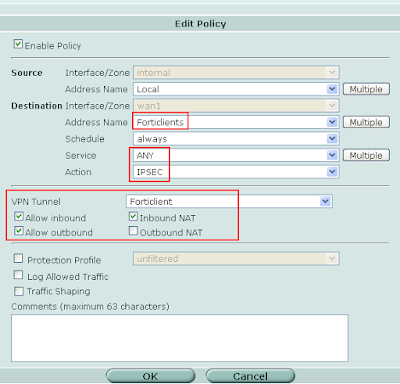
 10. Client Policy:
10. Client Policy:In this policy we select the "Forticlients" firewall address under the destination address name with the service set to "ANY" with the action of "IPSEC". Use the same VPN Tunnel properties as above.
So there you have it. Your all set on the serverside of this config. I will soon put up the client config to match this setup and allow you to connect. I will put up a brief overview of the FortiClient with it's various pros and cons. Please leave a comment if you have any questions.
No comments:
Post a Comment